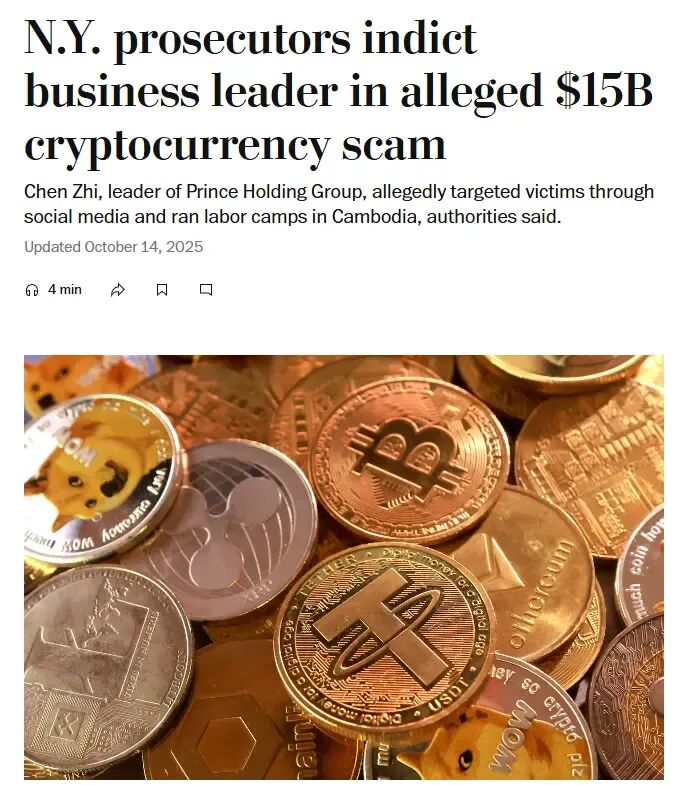
In October 2025, the US Department of Justice announced the largest cryptocurrency seizure in history, seizing 127,271 bitcoins, worth approximately $15 billion, from the notorious Cambodian "Prince Group" and its leader, Chin Chee. The plot of this event was dramatic and convoluted, resembling a cyber thriller.This operation has been hailed as a major victory in the global fight against transnational cybercrime and telecommunications fraud.

However, a groundbreaking technical analysis report released by the China National Computer Virus Emergency Response Center (CVERC) offers a completely different interpretation of this victory story, revealing a more complex and controversial truth: state-sponsored hacking, asset misappropriation, and a brutal "survival of the fittest" game, where fraud victims may have been doubly deceived.
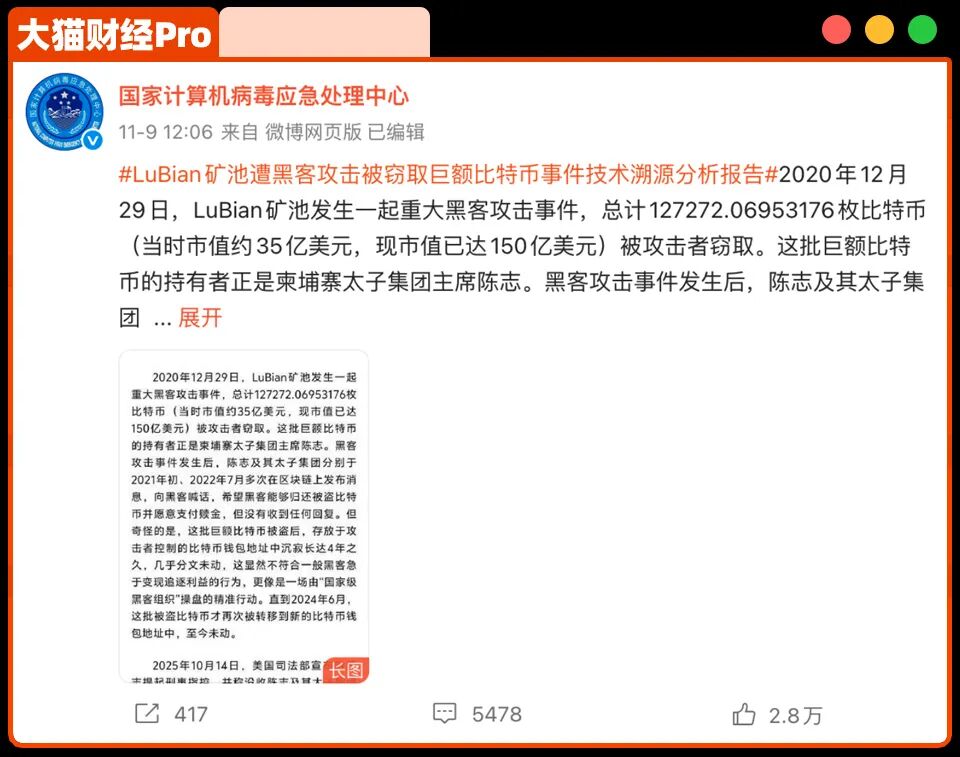
According to the official U.S. account detailed in the indictment, Chen Zhi and his "Prince Group" are portrayed as the masterminds behind a vast criminal empire.The group operates a large-scale "fraud camp" in Cambodia under the guise of legitimate real estate and financial businesses.It is alleged that within these camps, individuals were forced to carry out elaborate "sadomasochistic" scams, defrauding victims.These illicit proceeds were allegedly laundered through a complex network that included the group’s own Bitcoin mining operation, “Deerside Mining Pool”.The US judicial action, along with the asset freezes in the UK and Singapore, is seen as a decisive blow to this ubiquitous criminal network.However, this official account begins to fall apart once the timeline and technical details disclosed in the Chinese report are examined more closely.The core of the controversy is not the nature of the crimes Chen Zhi is accused of (although the crimes are serious), but the origin of the 127,271 bitcoins that the United States claims were legally seized.
According to a report released by CVERC on November 9, 2025, these Bitcoins did not belong to Chen Zhi, therefore the US had no right to seize them in October 2025. In fact, these Bitcoins were stolen five years ago.On December 29, 2020, the Lubian mining pool was hacked. Within two hours, 127,272 Bitcoins were transferred away by the hackers.Surprisingly, Lubian did not publicly acknowledge the theft, nor did the hackers come forward to "take responsibility."However, actions speak louder than words; Lubian quickly transferred the remaining Bitcoins away.What happened next? Of course, Lubian begged for their money back.Lubian started sending messages to the hackers, "Please return the money, we will pay a reward," hoping for amicable exchange.As a result, after spending 1.4 Bitcoins and sending over 1,500 messages, all of them went unanswered.Two years later, Lubian remained undeterred, continuing to send messages in an even more humble tone: "To the white-hat hackers who saved our assets, please contact us to discuss the return of our property and payment."

However, there was still no response, and the hacker's wallet remained untouched.But how exactly were the Bitcoins stolen?At that time, the hackers exploited a critical "pseudo-random number vulnerability" in the mining pool's digital wallet system.This vulnerability significantly reduced the security of the private key (the cryptographic key that controls Bitcoin), making it extremely vulnerable to brute-force attacks, resulting in the wallet being emptied of Bitcoin in just two hours.
The events that followed the 2020 hacking attacks were highly unusual and formed the basis for accusations of state involvement.Unlike cybercriminals who typically liquidate stolen assets quickly for profit, the hackers left a massive $3.5 billion in cash lying dormant in their digital wallets for nearly four years.This long period of silence was not broken until June 2024, when the hacker finally moved to a new address, which is quite different from typical hacker behavior.CVERC's report concludes that this patience and strategic restraint are more typical of a "nation-state hacking organization" than a criminal group.
The case became even more complicated when blockchain analytics firms, including Arkham Intelligence, later identified the final destination addresses of these Bitcoins as belonging to the U.S. government.This constitutes a series of compelling and unsettling events: the 2020 hack allegedly orchestrated by a U.S. entity, followed by a long period of silence, the asset consolidation in 2024, and finally, in 2025, a public “seizure” packaged as a law enforcement victory.This process demonstrates that the U.S. government is not merely seizing existing assets from criminals, but is effectively taking control of assets allegedly stolen by its subordinate agencies years ago—a significant move aimed at legally exonerating the origins of Bitcoin.
As detailed in the Chinese report, the technology behind the initial hacking attack reveals a profound warning regarding digital security.Bitcoin’s reputation for being “ironclad” based on the inviolability of its private keys has been proven to have a critical weakness: human error in the implementation of its security protocols.LuBian mining pool failed to use a cryptographically secure random number generator, thus creating a backdoor that was exploited with astonishing efficiency.This incident demonstrates that even the most decentralized technologies can become vulnerable if their underlying code is flawed, and sophisticated state actors are capable of identifying and exploiting these flaws.Beyond the technical complexities, the case has also raised serious questions about international law and the United States’ “long-arm jurisdiction.”
Legal experts point out that the United States' exercise of jurisdiction based on the presence of American victims effectively undermines the judicial sovereignty of other countries (in this case, Cambodia).The legal process has been criticized for its lack of transparency, particularly its failure to clearly demonstrate a direct link between the seized Bitcoin and the fraudulent activities alleged in the indictment.Therefore, Chen Zhi's lawyer argued that these assets were originally stolen goods, questioning the legal basis for their confiscation.Reports indicate that the North American Asian community is a key target for Prince Group.The billions of dollars in losses represent the life savings of countless individuals and families.Ironically, the funds stolen from the victims were converted into Bitcoin and may now be confiscated by the US government under the guise of legal proceedings, with no clear way to return them to the original victims.For Chinese victims, this is undoubtedly adding insult to injury. They watched helplessly as their severely damaged criminal proceeds were drawn into a complex international legal and political struggle, vividly demonstrating how their victim funds are being devoured in a brutal power struggle between criminal groups and world powers.

Ultimately, the seizure of $15 billion worth of Bitcoin powerfully reveals a new reality of global financial and cyber power.It shattered the myth of absolute anonymity and security in the cryptocurrency space, revealing that the strength of its infrastructure depends on its weakest link.More importantly, it reveals how digital assets can become pawns in the power struggles between nations.For many victims, especially those in the global Chinese community, this incident offers almost no solace.Their losses fueled the rise of the Chen Zhi empire and the subsequent accumulation of Bitcoin wealth, but now, in this conflict between criminal organizations and state actors accused of “survival of the fittest,” their losses may be forgotten.The lack of a truly just outcome—the hope of returning the funds to the victims—leaves a sobering story about the complex relationship between justice, sovereignty, and power in the digital age.



